This article describes how to properly create a certificate (both server and client) for a device in Niagara, and then sign it using an existing CA certificate. The article does not address the topic of creating a custom CA, this has already been described in Niagara - Certificates - Adding a custom trusted certification authority.
-
The first step is to log into the server/client platform (e.g., controller) and go to Certificate Management.
-
In the User Key Store tab, click the New button at the bottom of the view.
-
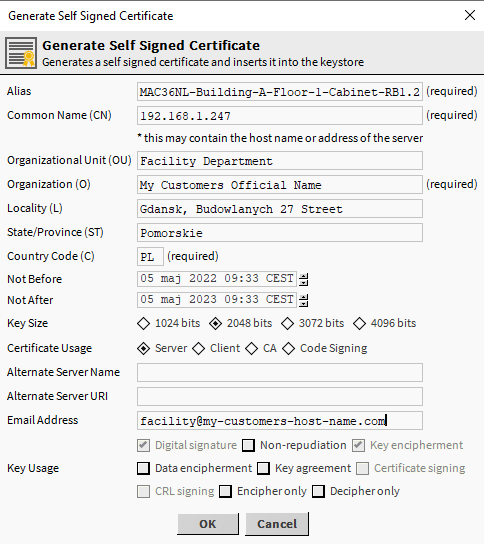
In the Generate Self Signed Certificate popup window, select server or client under Certificate Usage, depending on the destination, and then configure the certificate for the specified device.
-
Once approved, the server/client certificate will be generated and added to the list in the User Key Store tab. The added certificate should be checked, then click the Cert Request button at the bottom of the view. This will save the CSR file containing the created certificate.
-
Next, select Tools from the top menu and then Certificate Signer Tool, this will open the Certificate Signing popup window.
-
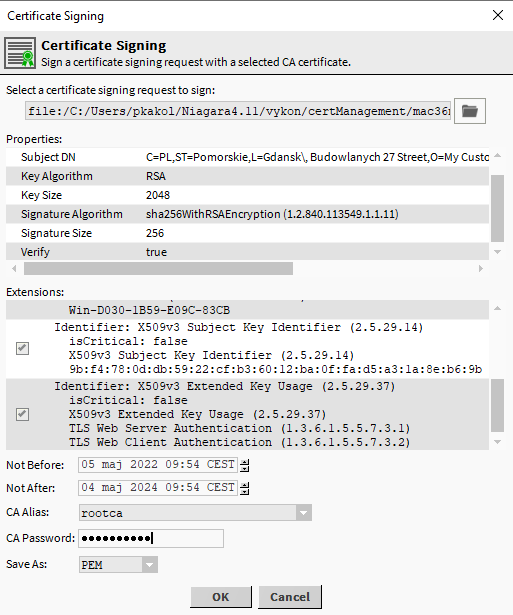
In the first field, select the CSR file of the server certificate to be signed, then select the CA Alias from the list (if you have not previously configured the custom CA, this list will be empty, and it will not be possible to perform a digital signature), and then in CA Password, enter the CA certificate private key password.
-
After approval, a popup window to save the PEM file of the signed server/client certificate will appear; if the window did not appear, it means that no CA Alias was selected and the process was not completed with the generation of the signed certificate.
-
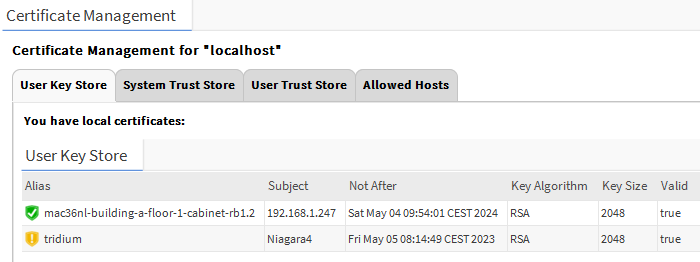
In the next step, in the User Key Store tab, click the Import button at the bottom of the view and select the PEM file of the signed server/client certificate in the popup window, and then approve it, so that the shield marking of the item in the list will change from yellow with an exclamation mark to green with a check mark.
-
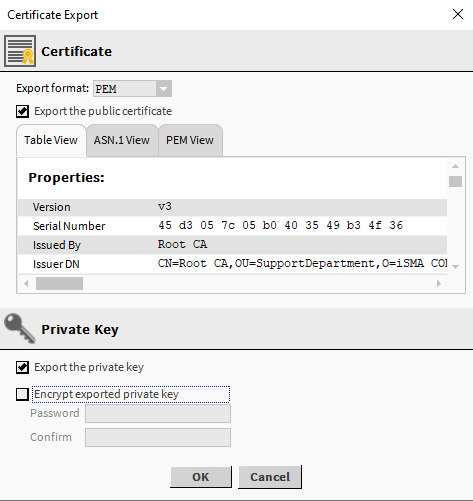
If the certificate was added in the wrong device, there is no need to to delete it and add it again in the target controller. The certificate can be exported with the public and private key to a PEM file by selecting it and clicking the Export buttons at the bottom of the view.
-
If necessary, encrypt the private key with a password. This is not required, but recommended.
-
Next, log in to the target host platform (e.g. driver), go to Certificate Management and in the User Key Store tab select the Import button, and in the popup window point to the PEM file with the exported public and private keys.
-
After pointing to the file, a popup window (Certificate Import) will appear with the details of the certificate. The certificate alias can be changed with the PEM file name automatically pulled as the alias.
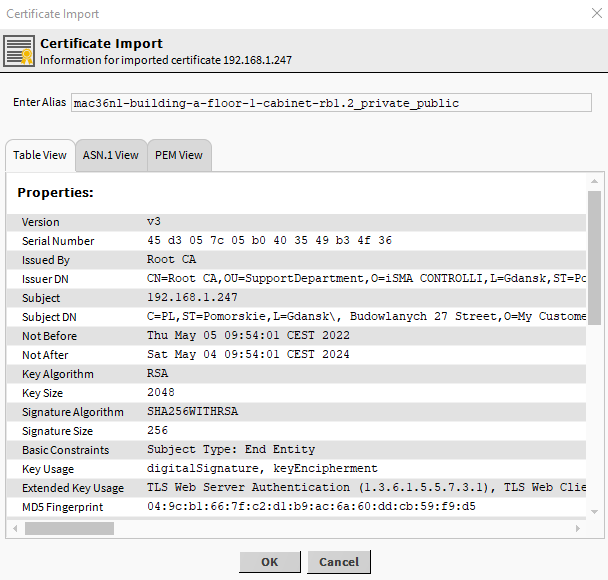
Server certificate
The server certificate is used in situations where the controller/Supervisor presents itself to clients connecting to it from the network. Here are basic examples of configuration and usage:
-
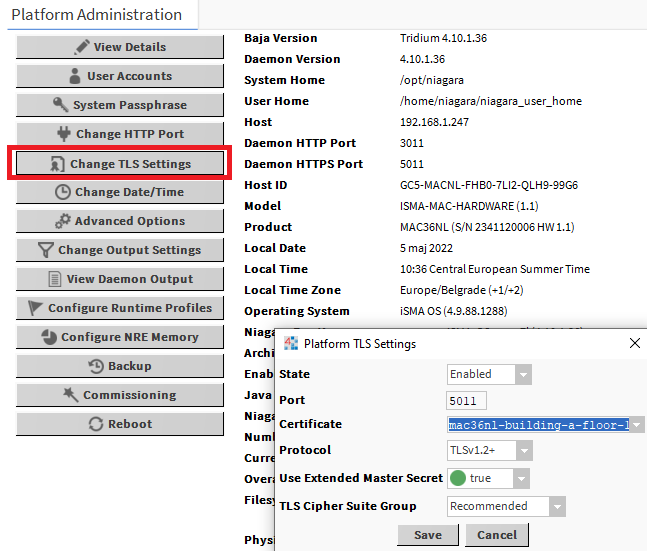
In the platform, go to Platform Administration and click Change TLS Settings and in the popup window change the tridium certificate to the custom one. This will make connecting to the platform using a digitally signed certificate.
-
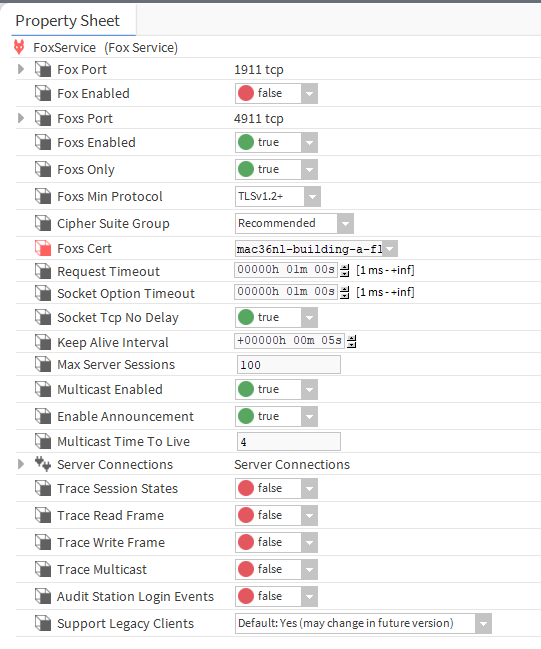
In the station, go to FoxService and in the Foxs Cert slot also indicate your certificate. This will ensure that connecting to the station is done with a digitally signed certificate.
-
In the station, go to WebService and in the Main Https Cert slot also indicate your certificate. This way, when connecting to the station from a web browser, the host will be marked with a certificate signed with our CA.
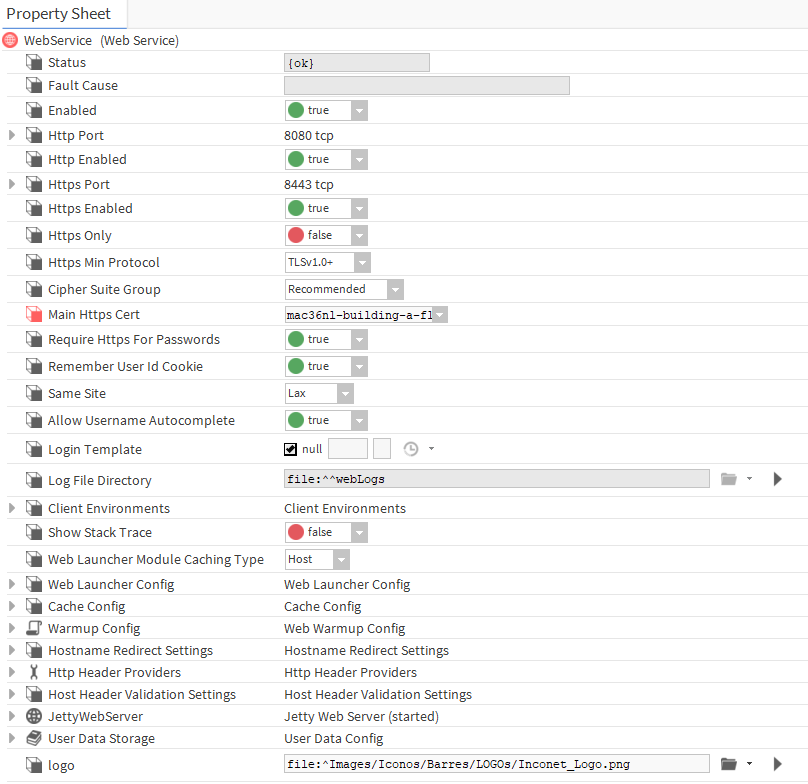
In order for the web browser to recognize the connection as secured, the public key of the CA with which the server certificate was signed must be added to the client's (e.g., computer's) certificate store.
-
When creating the configuration of the hub and client of BACnet/SC integration, server certificates are also needed, but this is described in the articles Niagara - BACnet/SC - Hub configuration and Niagara - BACnet/SC - Client configuration.
Client certificate
A client certificate is used in situations where a host presents itself as a trusted client to the servers to which it connects from the network.
